What’s Your Phishing IQ?
Find out why the Information Security Office focuses so often on Phishing and check your Phishing IQ with this brief quiz!
Question 1:
Industry generally estimates the percentage of all cyber incidents introduced from Phishing to be:
A.10-20%
B.20-60%
C.60-90%
Question 2:
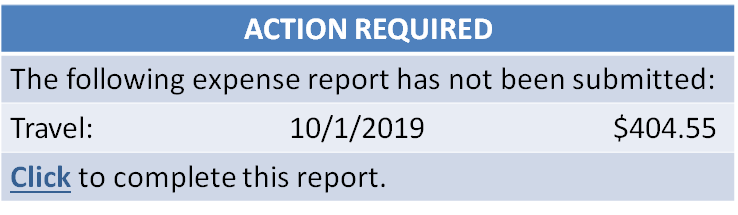
Review the example below. Phishing or real?
From: expense-noreply@gmail.com
Date: Fri, Nov 1, 2019 at 7:32 AM
Subject: Incomplete Expense Report
To:
Your Name,
Question 3:
Review the example below. Phishing or real?
From: PayPal <service@ppal.com>
Date: Tue, Oct 29, 2019 at 10:11 AM
Subject: Action required – user account suspended
To:
Your account has been suspended
Dear customer,
Our security system has detected an unauthorized payment attempt with your PayPal account.
For your security, your account has been suspended. A confirmation of your data is required to reactivate your account.
| Click Here to Confirm Identity |
Question 4:
Review the example below. Phishing or real?
From: GrubHub <billing@grubhub.com>
Date: Mon, Oct 21, 2019 at 5:10 PM
Subject: Your GrubHub Order
To:

Thank you for your purchase
Your order is on its way! Your delivery is expected within 25-30 minutes.
Didn’t place a GrubHub order? Please contact GrubHub customer assistance at grubhub.com or 888-999-0000.
Question 5:
Review the example below. Phishing or real?
From: Valid Employee <valid.employee@maine.edu.com>
Date: Thu, Oct 31, 2019 at 5:10 PM
Subject: CONFIDENTIAL DOCUMENT
To:
Please see attachment for your secure document.
You have received a secure File.
![]()
Document-004
Google Drive – create, share, and keep all your stuff in one place.
Answers:
- Industry generally estimates the percentage of all cyber incidents introduced through Phishing to be 60-90%.
- Phishing. The “From” email address is not a valid email address. Phish actors use oftenly-communicated messages (expense reports, payroll deductions, employment or customer loyalty incentives, etc.) to reach victims. Users may be tempted to click on the link, especially if, in this example, they have a recent legitimate expense report; or, to correct a seeming mistake by their employer. Don’t be fooled by content that is not relevant to you. If the content requests you click on a link, verify sender information and hover over the link to verify it is a legitimate link.
- Phishing. The “From” email address is not a valid email address. The content and request to click on a link are a clue to raise your suspicion. The logo looks valid, which is a tactic used by Phish actors, Even if you have an account with the apparent sender, check details carefully if the email asks you to log in to your account or take action that provides or leads to revealing your sensitive information. Phish actors will often use official-looking logos or pattern communication after legitimate formats that users recognize. Hover over links to check their validity. Contact your company independently to confirm the message.
- Real (assuming you placed a GrubHub order). The communication does not request you to reply, click on a link, or take a particular action. A number and website are included with instruction for report if you didn’t place a grubhub order. It is a good idea, if you didn’t place an order, to ignore the communication; if you decide to report the error, search for and visit the website from a new browser window, and use the contact information listed there.
- Phishing. The From email address is invalid. The lack of context in the message should be a clue that it is Phishing. Lastly, messages that request you to take an action (in this case, click on a document) should be cause for suspicion/verification. The tactic is often effective; the University does use Google services, and the Icon and Footer appears to look like Google icons and footers. The University does not use a secure Gmail solution that requires you to enter credentials to view a document, which is another clue. With the lack of context, or any other indication that this is not a secure document that you are expecting, verify with the sender or expected sender independently (create a new email message, chat or phone the sender).
Questions? Comments? Contact UMS Information Security at infosecurity@maine.edu.
(Content for this page was provided by Jean Schmidt, UMS Information Security Analyst)