SAFE COMPUTING

Smart Cyberdefense
Nefarious actors are increasing in sophistication. Tips for protecting yourself, and UMS:
- Protect your email accounts. Where practicable, use your UMS account solely for UMS purposes.
- Use strong passwords, and avoid reusing passwords for multiple accounts. If an account is compromised, accounts using the same password are vulnerable. Avoid using easily discernible passwords, passwords with personally identifiable information, or commonly available information such as birth date or address information.
- Download software, apps, web add-ons, plug-ins, and extensions only from trusted sources; and only current vendor-supported versions.
- Be careful with your personal information that you store online. Hackers use personal information for impersonation as well as answering “secret” security questions.
- Check online bank/financial accounts regularly. Hackers target W-2/W-4 tax profiles, and payroll/direct deposit information.
- Log off or lock unattended devices.
Phish Awareness
Phishing scams pose the greatest threat to the UMS, and are becoming more difficult to detect. By posing as a person or organization you trust, phish actors exploit victims for money, steal credentials or plant malware.
Tips for avoiding and preventing Phish attacks:
- Check sender and link information, in particular when receiving unexpected email, messaging, or social media communications, even if they appear to be from legitimate individuals.
- Do not reply to any request for your username and/or password, personal or UMS sensitive data, financial information; or communications that request you take action and/or take action to avoid consequence.
- Be cautious when clicking links in email, and when opening attached documents. Do not provide credentials (username/password) when opening attached documents or clicking links; check with the originator or UMS Information Security first to verify the authenticity of the communication.
- Be extra cautious of phishing when using a mobile device which might not show as many details, such as the sender’s true address.
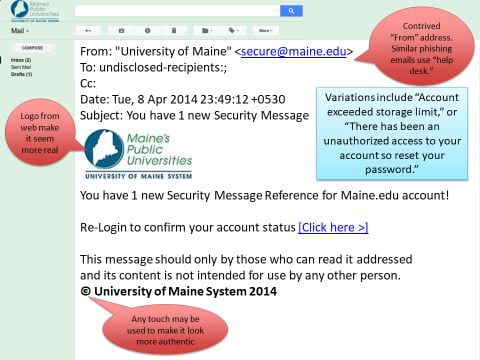
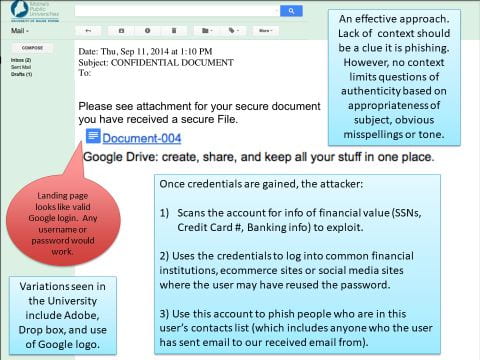
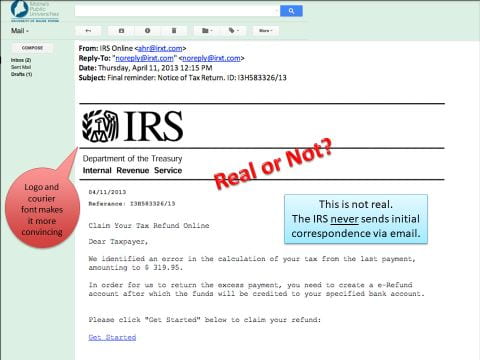
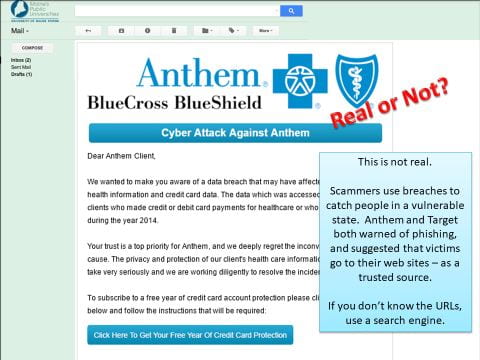
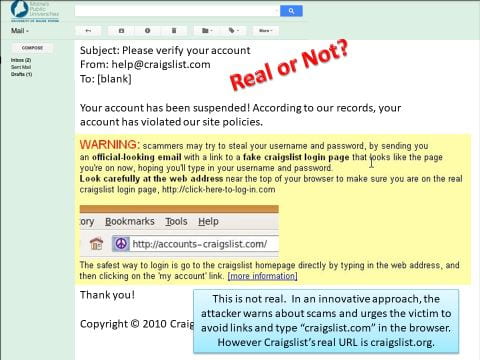
Examples of Sophisticated Phish Attacks
Questions? Comments? Contact UMS Information Security at infosecurity@maine.edu.
(Content for this page was provided by Jean Schmidt, UMS Information Security Analyst)